Subscribe to the Zog Blog to get news Delivered straight to Your box!
Newsletter Signup
Recent Posts
Archives
Archives
- November 2025 (1)
- September 2025 (1)
- May 2025 (1)
- March 2025 (1)
- November 2024 (1)
- October 2024 (1)
- August 2024 (1)
- July 2024 (1)
- June 2024 (1)
- May 2024 (1)
- December 2023 (2)
- November 2023 (1)
- August 2023 (1)
- June 2023 (1)
- May 2023 (1)
- April 2023 (1)
- December 2022 (4)
- November 2022 (3)
- October 2022 (2)
- September 2022 (2)
- August 2022 (3)
- July 2022 (2)
- May 2022 (3)
- April 2022 (2)
- March 2020 (1)
- November 2019 (1)
- October 2019 (2)
- September 2019 (3)
- August 2019 (2)
- July 2019 (5)
- June 2019 (3)
- May 2019 (2)
- April 2019 (1)
- March 2019 (2)
- August 2018 (2)
- July 2018 (1)
- June 2018 (1)
- May 2018 (4)
- April 2018 (5)
- March 2018 (2)
- February 2018 (3)
- January 2018 (3)
- December 2017 (3)
- November 2017 (2)
- October 2017 (3)
- September 2017 (4)
- August 2017 (2)
- July 2017 (4)
- June 2017 (4)
- May 2017 (5)
- April 2017 (4)
- March 2017 (3)
- February 2017 (4)
- January 2017 (5)
- December 2016 (4)
- November 2016 (5)
- October 2016 (4)
- September 2016 (3)
- August 2016 (4)
- July 2016 (1)

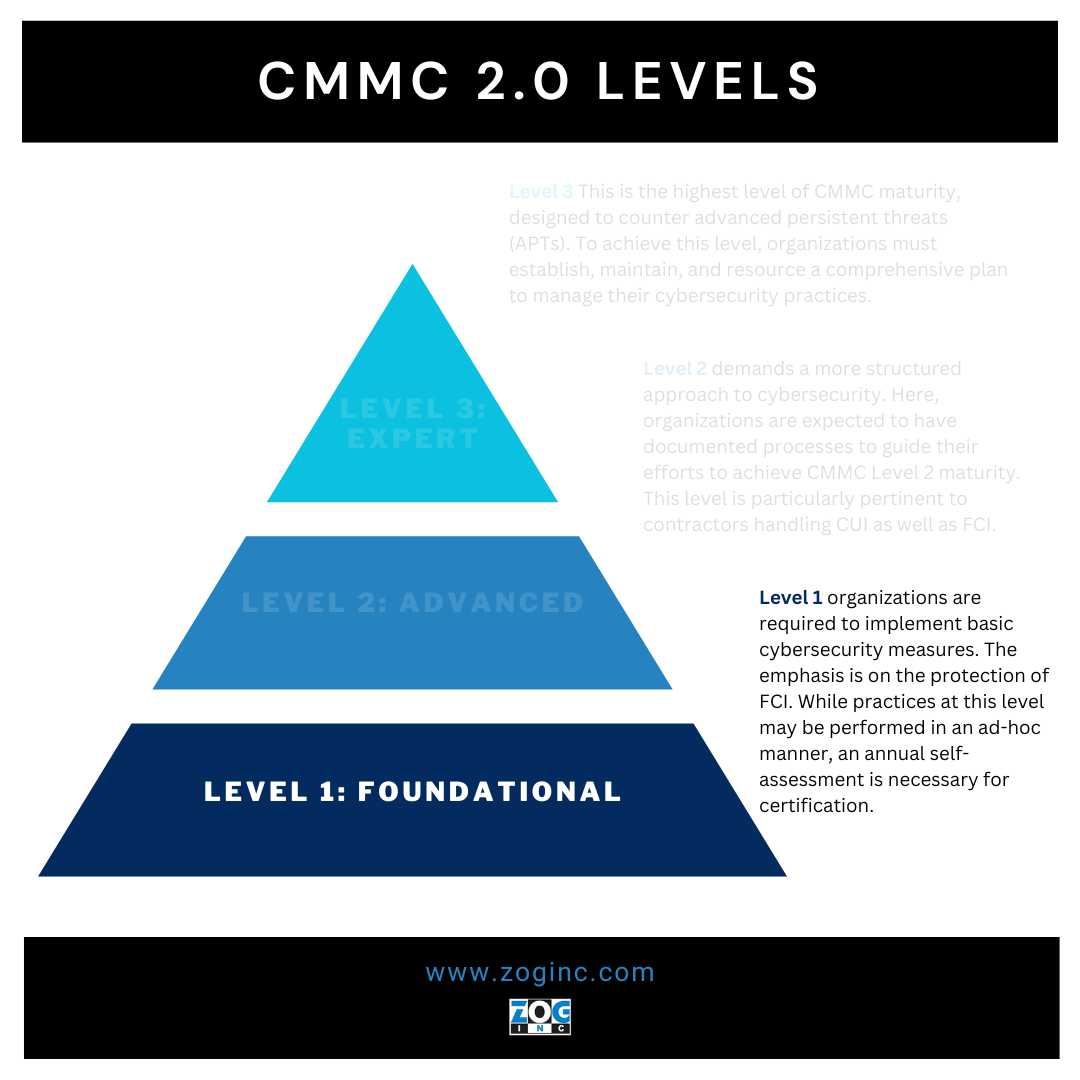
Your Essential Guide to Navigating CMMC 2.0 Level 1
For a deep dive into CMMC 2.0, be sure to read Zog’s Ultimate Guide to CMMC 2.0 Compliance. This post will focus solely on the entry-level tier of the certification model: CMMC 2.0 Level 1. CMMC Level 1 is all about establishing basic cyber hygiene.
We’ll overview the framework, requirements, self-assessment, and more.
Understanding the CMMC Framework
At a high level, CMMC is designed to protect the Defense Industrial Base (DIB) sector’s sensitive data, specifically Federal Contract Information (FCI) and Controlled Unclassified Information (CUI).
What is Federal Contract Information (FCI)?
Federal Contract Information (FCI) is information not intended for public release that is provided by or generated for the Government under a contract to develop or deliver a product or service to the government. FCI excludes information provided by the Government to the public, such as that on public websites, or simple transactional information, such as necessary to process payments.
What is Controlled Unclassified Information (CUI)?
Controlled Unclassified Information (CUI) is unclassified information that requires safeguarding in line with laws, regulations, and government-wide policies.
The Importance of CMMC Level 1
CMMC Level 1 serves as the foundation for all subsequent certification levels. It’s the cybersecurity equivalent of laying the groundwork for a house — you can’t build the walls and roof without first having a solid base. CMMC Level 1 provides this base, focusing on basic cyber hygiene practices that every defense contractor should implement to safeguard FCI.
CMMC Level 1 is about demonstrating basic cyber hygiene. It’s designed to be achievable for even smaller companies and includes a subset of universally accepted common security practices. CMMC Level 1 all about safeguarding FCI, which again, is provided by or generated for the Government under a contract to develop or deliver a product or service to the Government.
It’s important to note that while practices are expected to be performed, security process maturity isn’t addressed at CMMC Level 1. This means that an organization at this level may have limited or inconsistent cybersecurity maturity processes.
Aside from access to government contracts and enhanced cybersecurity posture, DoD contractors face strict penalties for non-compliance.
Non-compliance with CMMC could lead to the loss of DoD contracts and further penalties under the False Claims Act (FCA). In October 2021, the DOJ initiated their Civil Cyber-Fraud Initiative which aims to encourage whistleblowers to come forward against contractors falsely claiming to have implemented preventive cybersecurity practices. Violations can lead to penalties and fines with whistleblowers receiving anywhere between 15% — 25% of any reward resulting from a case.
CMMC Level 1 Requirements Checklist
Achieving CMMC Level 1 requires adherence to 17 specific controls, all mapped directly to the Federal Acquisition Regulation (FAR) 52.204.21. These controls are broken down into six categories: Access Control, Identification and Authentication, Media Protection, Physical Protection, System and Communications Protection, and System and Information Integrity.
When preparing for your self-assessment, have a clear process for verifying each of the following 17 controls.
Access Control (AC)
The Access Control (AC) domain focuses on managing and monitoring system and network access, including who has access, what level of access they have, and how they connect to external systems.
The following are the Level 1 AC controls:
- AC.1.001 — Limiting system access to authorized users, processes, or devices.
- AC.1.002 — Restricting system access to the transactions and functions that authorized users are allowed to perform.
- AC.1.003 — Verifying and controlling connections to, and use of, external information systems.
- AC.1.004 — Controlling information that is posted or processed on publicly accessible information systems.
Identification and Authentication (IA)
The Identification and Authentication (IA) domain focuses on identities within your organization and ensuring all system and network access is traceable for accountability purposes.
The Level 1 IA controls are:
- IA.1.076 — Identifying information system users, processes acting on behalf of users, and devices.
- IA.1.077 — Authenticating the identities of users, processes, or devices before granting access to organizational information systems.
Media Protection (MP)
Media Protection involves identifying, tracking, and maintaining media, including policies on protection, data sanitation, and acceptable transportation.
For Level 1, contractors are required to comply with one MP control:
- MP.1.118 — Sanitizing or destroying information system media containing FCI before disposal or reuse.
Physical Protection (PE)
Physical Protection is an often overlooked domain that involves limiting physical access to systems, equipment, and operating environments to authorized personnel.
Level 1 PE controls are:
- PE.1.131 — Limiting physical access to organizational information systems, equipment, and the respective operating environments to authorized individuals.
- PE.1.132 — Escorting visitors and monitoring visitor activity.
- PE.1.133 — Maintaining audit logs of physical access.
- PE.1.134 — Controlling and managing physical access devices.
System and Communication Protection (SC)
The System and Communication Protection (SC) domain is devoted to securing internal and external communications within an organization. The Level 1 SC control requirements are:
- SC.1.175 — Monitoring, controlling, and protecting organizational communications at the external boundaries and key internal boundaries of information systems.
- SC.1.176 — Implementing subnetworks for publicly accessible system components that are physically or logically separated from internal networks.
System and Information Integrity (SI)
The System and Information Integrity (SI) domain focuses on the ongoing maintenance and management of issues within information systems. The Level 1 SI controls are:
- SI.1.210 — Identifying, reporting, and correcting information and information flaws in a timely manner.
- SI.1.211 — Providing protection from malicious code at appropriate locations within organizational information systems.
- SI.1.212 — Updating malicious code protection mechanisms when new releases are available.
- SI.1.213 — Performing periodic scans of information systems and real-time scans of files from external sources as files are downloaded, opened, or executed.
CMMC Level 1 Certification & Self-Assessment
What Does CMMC Level 1 “Self-Assessed” Mean?
Unlike other certifications or CMMC levels that require external audits and/or third-party validation, CMMC Level 1 offers a self-assessed certification. This puts the onus on contractors, requiring them to evaluate and verify their own compliance (they can do so with the help of a third-party like Zog, Inc.).
Guidance for the CMMC Level 1 Self-Assessment
To assist contractors in this self-assessment process, the DoD provides the CMMC Level 1 Assessment Guide which is a comprehensive set of criteria and best practices for contractors to follow. The CMMC Level 1 Assessment Guide is derived from the National Institute of Standards and Technology (NIST) Special Publication (SP) 800–171A — specifically Section 2.1.
The CMMC Level 1 Assessment Guide serves as a foundational resource, ultimately giving contractors a clear and consistent framework.
Reporting Your Self-Assessment Results
After self-assessment, contractors’ results are shared with the DoD by way of the Supplier Performance Risk System (SPRS), a centralized platform used to review and monitor the compliance of its contractors.
FAQs:
How can DoD Contractors ensure they meet all the necessary criteria for CMMC 2.0 Level 1?
Contractors should be familiar with the 17 foundational requirements covered in this post. Having these practices in place is a solid foundation for transitioning to CMMC Level 2. Organizations should designate an expert who understands these requirements and whose job it is to maintain a centralized portal for easy access to all related CMMC Level 1 information. Tools and technology can assist contracts with staying organized and prepared for compliance audits.
Are there any specific tools or software solutions recommended for DoD Contractors to help with CMMC 2.0 Level 1 compliance?
The market offers a plethora of tools, making it crucial to choose those that offer compliance tracking capabilities. Zog, Inc. gives preferences to tools that can address multiple compliance frameworks (CMMC, HIPAA, etc.) as it enables contractors to handle various audits and compliance requirements in a more streamlined fashion.
What are the best practices for DoD Contractors to prepare for a CMMC 2.0 Level 1 audit?
When preparing for a CMMC Level 1 audit, contractors should be equipped with the right compliance tools and also invest in cybersecurity solutions that align with the specified practices in their chosen frameworks (CMMC for example). Zog, Inc. advises having the cybersecurity program run separate from the IT Department to ensure unbiased oversight. Rather than conducting self-audits, it’s more beneficial and transparent to engage with a third party for audit purposes. For instance, if Zog, Inc. is an organization’s IT partner, it’s crucial that Zog, Inc. also employs a third party for audits to guarantee impartial evaluations.
How can DoD Contractors stay updated on any changes or updates related to CMMC 2.0 Level 1 requirements?
Responsibility for staying on top of changes to CMMC Level 1 requirements usually falls on organizations like Zog, Inc. or other compliance entities. It’s important to conduct regular reviews and make necessary updates when applicable. Zog, Inc. adopts a proactive stance by annually updating programs, reflecting the most recent changes and trends in the security sector. This ultimately ensures clients remain well-informed and ahead of cybersecurity.
What is FCI?
FCI stands for Federal Contract Information. FCI is information or data provided by or generated for the Government under a contract and not intended for public release.
The Value of CMMC Level 1
CMMC Level 1 lays the foundation for DoD contractors interested or required to seek subsequent CMMC certification levels while simultaneously shining light on how serious contractors are taking cybersecurity (both of their own systems and sensitive Government data).


Leave a Comment
Your email address will not be published. Required fields are marked *