Subscribe to the Zog Blog to get news Delivered straight to Your box!
Newsletter Signup
Recent Posts
Archives
Archives
- March 2025 (1)
- November 2024 (1)
- October 2024 (1)
- August 2024 (1)
- July 2024 (1)
- June 2024 (1)
- May 2024 (1)
- December 2023 (2)
- November 2023 (1)
- August 2023 (1)
- June 2023 (1)
- May 2023 (1)
- April 2023 (1)
- December 2022 (4)
- November 2022 (3)
- October 2022 (2)
- September 2022 (2)
- August 2022 (3)
- July 2022 (2)
- May 2022 (3)
- April 2022 (2)
- March 2020 (1)
- November 2019 (1)
- October 2019 (2)
- September 2019 (3)
- August 2019 (2)
- July 2019 (5)
- June 2019 (3)
- May 2019 (2)
- April 2019 (1)
- March 2019 (2)
- August 2018 (2)
- July 2018 (1)
- June 2018 (1)
- May 2018 (4)
- April 2018 (5)
- March 2018 (2)
- February 2018 (3)
- January 2018 (3)
- December 2017 (3)
- November 2017 (2)
- October 2017 (3)
- September 2017 (4)
- August 2017 (2)
- July 2017 (4)
- June 2017 (4)
- May 2017 (5)
- April 2017 (4)
- March 2017 (3)
- February 2017 (4)
- January 2017 (5)
- December 2016 (4)
- November 2016 (5)
- October 2016 (4)
- September 2016 (3)
- August 2016 (4)
- July 2016 (1)

Zog’s Ultimate Guide to CMMC 2.0 Compliance (+ Bonus Checklist)
CMMC stands for Cybersecurity Maturity Model Certification.
The Cybersecurity Maturity Model Certification (CMMC) 2.0 is the latest security standard put forth by the U.S. Department of Defense (DoD). It’s a benchmark that organizations must meet to secure contracts with the DoD.
Zog’s Ultimate Guide to CMMC Compliance will overview CMMC 2.0, cover implications for contractors, and overview how organizations can achieve compliance.
Table of Contents
- What is CMMC?
- Why is CMMC 2.0 Compliance Important?
- What are the Purpose and Goals of CMMC?
- Who Needs CMMC Certification?
- Evolution of CMMC: From 1.0 to 2.0
- CMMC 2.0 Framework: An Overview
- CMMC 2.0 Levels: A Detailed Look
- CMMC Domains: Breaking Down the 17 Core Security Domains
- Determining Your CMMC Level
- Differences Between CMMC 2.0 and NIST 800-171
- Steps to Achieve CMMC Compliance
- Performing a CMMC Self-Assessment
- CMMC Roles and Responsibilities
- Navigating CMMC Certification Challenges
- Implications of CMMC 2.0 for DoD Contractors
- Timeline for CMMC Implementation
- How to Prepare for CMMC 2.0 Compliance
- CMMC 2.0 Compliance Checklist
- Post-Certification: Maintaining and Improving Compliance
- Frequently Asked CMMC Questions
What is CMMC?
CMMC, or Cybersecurity Maturity Model Certification, is a unified cybersecurity standard developed by the DoD. CMMC ultimately exists in an effort to protect the Defense Industrial Base (DIB) — the network of private-sector companies providing goods and services to the DoD while aiming to enhance cybersecurity practices and processes, ensuring the protection of sensitive data – specifically Federal Contract Information (FCI) and Controlled Unclassified Information (CUI).
Why is CMMC 2.0 Compliance Important?
There are several reasons why achieving CMMC 2.0 compliance is essential:
- Access to Government Contracts: Compliance with CMMC 2.0 levels is a prerequisite for organizations seeking to bid on or maintain contracts with the Department of Defense.
- Enhanced Cybersecurity Posture: Implementing the required security controls strengthens an organization’s cybersecurity defenses, reducing the risk of cyberattacks and data breaches.
- Regulatory Compliance: Adherence to CMMC 2.0 demonstrates an organization’s commitment to meeting federal cybersecurity requirements and industry best practices.
What are the Purpose and Goals of CMMC?
CMMC’s purpose is to enhance the cybersecurity posture of organizations participating in the defense supply chain and achieves this via verifiable cybersecurity practices and processes. Companies must meet a specific level of cyber maturity before being awarded DoD contracts which ensures a greater likelihood that sensitive data and information stay secure throughout the supply chain.
Who Needs CMMC Certification?
Businesses aiming to work with or maintain existing contracts with the DoD must demonstrate their commitment to cybersecurity by complying with CMMC.
Evolution of CMMC: From 1.0 to 2.0
CMMC 1.0 incorporated five certification levels – 1) basic cyber hygiene, 2) intermediate cyber hygiene, 3) good cyber hygiene, 4) proactive, and 5) advanced / progressive. One of the most obvious changes from CMMC 1.0 to CMMC 2.0 is the number of certification levels as CMMC 2.0 consists of just three – 1) foundational, 2) advanced, and 3) expert. CMMC 2.0 also introduced the opportunity for certain organizations to self-assess their compliance which aims to eliminate barriers to DoD contracts.
CMMC 2.0 Framework: An Overview
As we just covered, the CMMC 2.0 framework is made up of three maturity levels – foundational, advanced, and expert. Each level embodies cybersecurity practices and processes contractors must comply with to achieve that specific certification. CMMC is built on the U.S. National Institute of Standards and Technology (NIST) family of standards. Organizations adhering to the framework are in turn boosting their overall cybersecurity posture.
CMMC 2.0 Levels: A Detailed Look
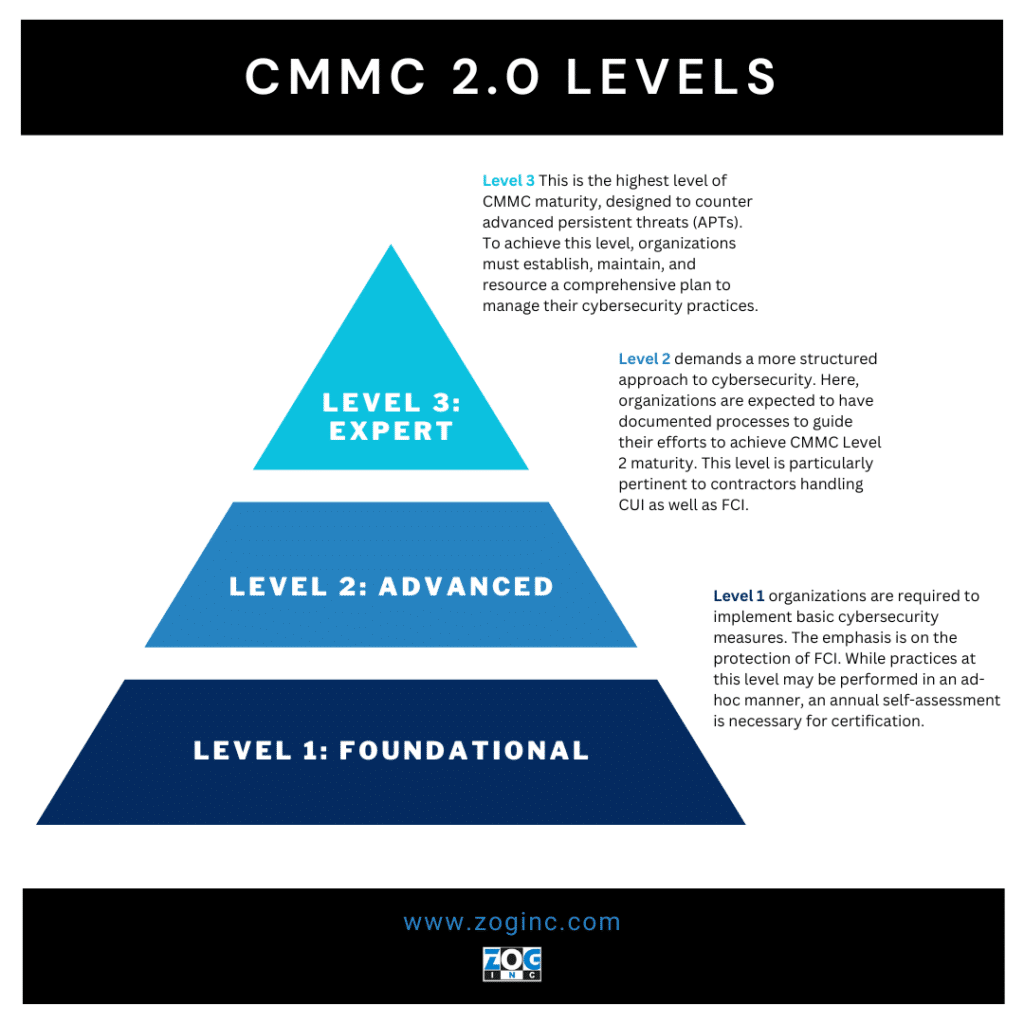
CMMC 2.0 Level 1: Foundational
At this level, organizations are required to implement basic cybersecurity measures. The emphasis is on the protection of FCI. While practices at this level may be performed in an ad-hoc manner, an annual self-assessment is necessary for certification.
Certification at this level is achievable through an annual self-assessment, eliminating the need for C3PAOs to assess process maturity for level 1. The main focus at this level lies in the protection of FCI, adhering to the basic safeguarding requirements described in 48 CFR 52.204-21.
Who Needs CMMC Level 1?
DoD contractors and subcontractors handling Federal Contract Information (FCI), or “Information not intended for public release [that] is provided by or generated for the Government under a contract to develop or deliver a product or service to the Government,” need CMMC Level 1 certification.
CMMC 2.0 Level 2: Advanced
Level 2 demands a more structured approach to cybersecurity. Here, organizations are expected to have documented processes to guide their efforts to achieve CMMC Level 2 maturity. This level is particularly pertinent to contractors handling CUI as well as FCI. However, the assessment requirements vary based on the criticality of the CUI data being handled.
The practices at Level 2 are classified as advanced cyber hygiene practices, often referred to as intermediate cyber hygiene, marking a progression between levels 1 and 3. CMMC 2.0 Level 2 aligns with CMMC 1.02 Level 3, based on NIST SP 800-171.
The assessment requirements for Level 2 compliance vary based on the criticality of the CUI data. Organizations with prioritized acquisitions handling data critical to national security must pass a higher-level third-party assessment (C3PAOs) every three years. However, non-prioritized acquisitions with data not critical to national security must conduct an annual self-assessment.
Who Needs CMMC Level 2?
DoD contractors and subcontractors handling the same type of Controlled Unclassified Information (CUI) must meet Level 2 compliance. A lower CMMC level may apply to the subcontractor if the prime contractor only flows down selected information.
CMMC 2.0 Level 3: Expert
This is the highest level of CMMC maturity, designed to counter advanced persistent threats (APTs). To achieve this level, organizations must establish, maintain, and resource a comprehensive plan to manage their cybersecurity practices.
The cybersecurity practices at this level qualify as good cyber hygiene practices and focus on protecting CUI. They encompass all the security requirements specified in NIST SP 800-171, and the additional 20 practices added for CMMC level 2.
CMMC 2.0 Level 3 applies to companies that handle CUI for DoD programs with the highest priority. It’s comparable to CMMC 1.02 Level 5, but the DoD is still in the process of developing its specific security requirements.
Who Needs CMMC Level 3?
DoD contractors and subcontractors handling the same type of Controlled Unclassified Information (CUI) must meet Level 3 compliance. A lower CMMC level may apply to the subcontractor if the prime contractor only flows down select information.
CMMC Domains: Breaking Down the 17 Core Security Domains
The CMMC 2.0 framework categorizes cybersecurity practices into 17 domains, with 43 capabilities associated with these domains. The capabilities that a contractor must demonstrate are dependent on their required CMMC level. The domains cover a broad spectrum of cybersecurity aspects, from Access Control and Asset Management to System and Communications Protection and System and Information Integrity.
Here’s a comprehensive breakdown of the 43 CMMC capabilities and their association with the 17 domains of the CMMC 2.0 model:
Access Control (AC)
- Establish system access requirements
- Control internal system access
- Control remote system access
- Limit data access to authorized users and processes
Asset Management (AM)
- Identify and document assets
Audit and Accountability (AU)
- Define audit requirements
- Perform auditing
- Identify and protect audit information
- Review and manage audit logs
Awareness and Training (AT)
- Conduct security awareness activities
- Conduct training
Configuration Management (CM)
- Establish configuration baselines
- Perform configuration and change management
Identification and Authentication (IA)
- Grant access to authenticated entities
Incident Response (IR)
- Plan incident response
- Detect and report events
- Develop and implement a response to a declared incident
- Perform post-incident reviews
- Test incident response
Maintenance (MA)
- Manage maintenance
Media Protection (MP)
- Identify and mark media
- Protect and control media
- Sanitize media
- Protect media during transport
Personnel Security (PS)
- Screen personnel
- Protect CUI during personnel actions
Physical Protection (PE)
- Limit physical access
Recovery (RE)
- Manage back-ups
Risk Management (RM)
- Identify and evaluate risk
- Manage risk
Security Assessment (CA)
- Develop and manage a system security plan
- Define and manage controls
- Perform code review
Situational Awareness (SA)
- Implement threat monitoring
System and Communications Protection (SC)
- Define security requirements for systems and communications
- Control communications at system boundaries
System and Information Integrity (SI)
- Identify and manage information system flaws
- Identify malicious content
- Perform network and system monitoring
- Implement advanced email protections
Organizations can demonstrate compliance with these capabilities by adhering to a range of practices and processes. The practices are the technical activities of each capability, consisting of 171 practices mapped across the three CMMC levels.
Determining Your CMMC Level
The DoD will specify the required CMMC level in the contract solicitation. The level needed is determined by the type and sensitivity of the data an organization will be handling. For instance, contractors handling only FCI will need to meet the requirements of CMMC Level 1. In contrast, those dealing with CUI will need to achieve Level 2 or Level 3 compliance, depending on the criticality of the data.
Differences Between CMMC 2.0 and NIST 800-171
While CMMC 2.0 draws heavily from the NIST SP 800-171 standard, it differs in several significant ways. One key distinction is the transition from self-assessment to independent third-party assessments for compliance. This shift enhances accountability and accuracy, ensuring that non-compliance with DoD cybersecurity regulations is not acceptable.
Steps to Achieve CMMC Compliance
Achieving CMMC compliance, especially for contractors handling CUI and needing to reach CMMC Level 2 or higher, requires a proactive, comprehensive approach to security. This approach includes the following steps:
- Understand the Requirements: Familiarize yourself with the security controls outlined in the NIST SP 800-171 guidelines and the CMMC framework.
- Conduct a Gap Analysis: Evaluate your organization’s current cybersecurity practices, identify gaps, and develop a plan to address them.
- Policies and Procedures: Develop, document, and implement comprehensive cybersecurity policies and procedures that align with CMMC requirements. Ensure that these policies are communicated across the organization and are regularly reviewed and updated.
- System Security Plan: Create a detailed System Security Plan (SSP) that outlines how your organization manages and protects Federal Contract Information (FCI) and Controlled Unclassified Information (CUI). This plan should describe the security controls in place, their implementation, and how they are managed.
- Implement Security Controls: Introduce necessary security controls to meet the CMMC 2.0 requirements, ensuring proper documentation and training.
- Engage a CMMC Third-Party Assessment Organization (C3PAO): Schedule and conduct an official CMMC assessment to verify your organization’s compliance with Level 1 requirements.
- Maintain Compliance: Continuously monitor and update your organization’s cybersecurity practices to ensure ongoing compliance with CMMC 2.0 requirements.
Performing a CMMC Self-Assessment
Under CMMC 2.0, organizations can perform self-assessments for Level 1 compliance, which does not require third-party validation or certification. However, the organization must submit an attestation signed by a senior executive, affirming the self-assessment has been conducted following the Assessment Guide.
To assist with this process, the US Department of Defense has published the Self-Assessment Guide for CMMC Level 1. You can download the guide from the Office of the Secretary of Defense’s website or use free self-assessment tools available online.
CMMC Roles and Responsibilities
Implementing the Cybersecurity Maturity Model Certification (CMMC) within an organization requires the involvement and cooperation of various roles, each having distinct responsibilities. Here’s a general outline of the roles and their associated responsibilities:
Senior Management (CEO, Board Members):
- Setting the organization’s overall strategic direction for cybersecurity.
- Allocating adequate resources (financial, human, technological) for CMMC implementation.
- Providing ultimate approval of cybersecurity policies and procedures.
- Fostering a cybersecurity-conscious culture within the organization.
CMMC Project Manager:
- Overseeing the entire CMMC compliance project.
- Developing and managing project plans, timelines, resources, and milestones.
- Coordinating with different teams and departments involved in the compliance process.
- Ensuring communication and collaboration amongst stakeholders.
Chief Information Security Officer (CISO)/Security Manager:
- Developing and maintaining the organization’s cybersecurity strategy in line with CMMC requirements.
- Supervising the execution of the cybersecurity plan.
- Overseeing regular risk assessments and implementing risk mitigation strategies.
- Advising senior management on cybersecurity issues and progress towards CMMC compliance.
IT Team:
- Implementing, managing, and maintaining the technical controls necessary for CMMC compliance.
- Collaborating with the CISO/Security Manager to integrate security into IT infrastructure.
- Conducting regular system checks and updates to keep security measures up-to-date.
Compliance Officer:
- Keeping up-to-date with CMMC requirements and guidelines.
- Ensuring all aspects of the organization are adhering to the set standards and policies.
- Conducting internal audits and inspections to check for compliance.
- Documenting compliance efforts for audit purposes.
HR Department:
- Implementing security awareness and training programs to help staff understand their roles in maintaining cybersecurity.
- Including CMMC-related obligations in job descriptions and contracts where necessary.
- Managing personnel security, including background checks if required.
All Employees:
- Following the organization’s cybersecurity policies and procedures.
- Attending mandatory cybersecurity training.
- Reporting any identified security issues or incidents to the appropriate person or department.
Third-Party Assessment Organizations (C3PAO):
- Conducting the official CMMC assessment.
- Providing pre-assessment guidance and post-assessment feedback.
- Issuing the CMMC certification upon successful completion of the assessment.
Navigating CMMC Certification Challenges
Common Pitfalls and Mistakes
The most common pitfalls and mistakes during the CMMC compliance process include underestimating the scope of CUI, overlooking third-party risks, and failing to allocate sufficient resources needed for compliance efforts.
Cost Considerations and Budgeting
Another challenge organizations face during and after the CMMC compliance process relates to budgeting. Technology investments, consulting fees, and internal resources are all necessary, making budgeting for these expenses a must.
Balancing Business Objectives with Security Requirements
Another common challenge for organizations is a result of competing priorities. Business success, operational efficiencies, innovation, and growth remain priorities for businesses, regardless of whether or not they’re seeking CMMC compliance. Leaders of these organizations striving for CMMC 2.0 compliance should find balance between business success and cybersecurity best practices.
Managing Change and Resistance Within the Organization
When it comes to transformational change, resistance is not uncommon. Given the vast scope of CMMC, it is important for business leaders and stakeholders to communicate the importance, early and often. Provide training and support throughout the process so employees feel part of the journey and less likely to resist change.
Implications of CMMC 2.0 for DoD Contractors
CMMC 2.0 comes with a significant shift in how DoD contractors need to think about and approach cybersecurity.
With the phasing out of Plans of Action & Milestones (POA&M) and the introduction of third-party audits, contractors have to be more proactive in their cybersecurity measures. Prime contractors also have to ensure that their subcontractors are compliant with the CMMC level appropriate to the sensitivity of the data they handle.
Contractors must meet the requirements for the level they’re seeking in both practices and processes. For example, a contractor could achieve Level 3 for practices and Level 2 on processes. In this case, the contractor will be certified at the lower level, CMMC Level 2.
Contractors need to begin preparing for CMMC now rather than waiting until they receive a contract with an actual CMMC requirement.
This preparation requires significant time, so failure to prepare now could result in the loss of a contract later.
Timeline for CMMC Implementation
The DoD plans to gradually increase the number of contracts requiring CMMC certification over the coming years. By 2026, all contractors working with the DoD, barring those dealing only with commercial off-the-shelf software, must comply with CMMC. Given this timeline, it’s crucial for contractors to start preparing for CMMC now to avoid any potential disruption to their business operations. It’s worth noting that a full implementation of the necessary changes to achieve CMMC compliance can be expected to take between 12 to 18 months. Early preparation is essential to ensure timely compliance.
How to Prepare for CMMC 2.0 Compliance
While the journey to CMMC compliance varies from one organization to another, experts recommend a number of best practices, categorized by phase, including baselining, implementation, enactment, and assessment.
Baselining
- Develop a plan with a consultant for achieving your desired level of compliance.
- Determine if you manage CUI and how you will protect it.
- Create a gap assessment between your company’s current capabilities and where they need to be.
- Create POAMs for the controls you don’t currently meet.
Implementation
- Implement the action items identified in the POAMs.
- Implement the procedures, training, and tools needed to close the gaps identified in the gap assessment.
Enactment
- Implement necessary monitoring of systems.
- Train your employees on the new security requirements.
- Resolve outstanding issues. Work through the SSP and adjust your time table accordingly.
Assessment
- Undergo an audit by a C3PAO.
- Prepare to present audit proof/evidence that required controls have been met and are documented correctly.
- Prepare for continuous improvement.
CMMC 2.0 Compliance Checklist
Achieving CMMC 2.0 compliance requires a systematic approach. Here is a comprehensive checklist to guide you on your compliance journey:
✔️ Understanding CMMC:
- Grasp the core concept of CMMC and its significance in cybersecurity.
- Recognize the importance of protecting Controlled Unclassified Information (CUI) and Federal Contract Information (FCI).
- Understand the consequences of non-compliance.
✔️ Determining CMMC Requirements:
- Identify if your organization is part of the Defense Industrial Base (DIB) sector.
- Determine if your contracts involve CUI or FCI.
- Familiarize yourself with the Defense Federal Acquisition Regulation Supplement (DFARS) requirements related to CMMC.
✔️ Identifying CMMC Domains and Practices:
- Break down the 17 domains and understand the specific practices within each.
- Prioritize domains based on your organization’s operations and data handling.
- Establish a roadmap for implementing required practices.
✔️ Understanding CMMC Compliance Levels:
- Familiarize yourself with the three levels of CMMC compliance.
- Determine the appropriate level for your organization based on contract requirements.
- Understand the progression and prerequisites for each level.
✔️ Starting CMMC Compliance Journey:
- Conduct a thorough assessment of where CUI is stored, processed, and transmitted within your organization.
- Evaluate current security measures and identify gaps in compliance.
- Develop a strategy for addressing identified gaps and enhancing cybersecurity posture.
✔️ Understanding Key CMMC Terms:
- Dive deep into terms like C3PAO (Certified Third-Party Assessment Organizations) and its role in the assessment process.
- Understand the significance of CMMC-AB (CMMC Accreditation Body) and its oversight functions.
- Familiarize yourself with the standards like NIST SP 800-171 and NIST SP 800-172 and their relevance to CMMC.
- Grasp the meaning and implications of terms like OSC (Organization Seeking Certification), POAM (Plan of Action & Milestones), and RPO (Registered Practitioner Organization).
✔️ Getting Ready for CMMC Compliance:
- Develop a comprehensive plan detailing the steps towards achieving compliance.
- Allocate necessary resources, including budget, personnel, and tools.
- Engage with a C3PAO for pre-assessment consultation.
- Prepare all necessary documentation, policies, and procedures.
- Conduct internal audits to ensure readiness for the official CMMC assessment.
- Address any findings from internal audits and refine processes as needed.

Post-Certification: Maintaining and Improving Compliance
Ongoing Monitoring and Risk Management
Your organization’s CMMC compliance doesn’t end after your certification. In fact, you can look at your certification as the beginning of a new normal. Continue monitoring the cyberthreat landscape and keeping ahead of potential risks. Aim to improve your cybersecurity posture over time.
Regularly Reviewing And Updating Policies And Procedures
Periodically review and update your organization’s policies and procedures to ensure they remain relevant, effective, and aligned with CMMC requirements.
Employee Training and Awareness Programs
It’s no secret that the majority of cyberattacks start at the employee level. Regular, ongoing, and structured employee training and awareness help organizations reinforce best practice. Help staff stay in the know of evolving threats, ensuring employee education is aligned with your CMMC certification requirements.
Preparing for Recertification and Audits
With compliance comes the need for recertification and the potential for audits. You can ensure your organization is prepared for the inevitable with ongoing, thorough documentation of your cyber practices, policies, and procedures.
Frequently Asked CMMC Questions
CMMC, or Cybersecurity Maturity Model Certification, is a unified cybersecurity standard developed by the DoD. CMMC ultimately exists in an effort to protect the Defense Industrial Base (DIB) — the network of private-sector companies providing goods and services to the DoD while aiming to enhance cybersecurity practices and processes, ensuring the protection of sensitive data – specifically Federal Contract Information (FCI) and Controlled Unclassified Information (CUI).
There are several reasons why achieving CMMC 2.0 compliance is essential: Access to Government Contracts: Compliance with CMMC 2.0 levels is a prerequisite for organizations seeking to bid on or maintain contracts with the Department of Defense. Enhanced Cybersecurity Posture: Implementing the required security controls strengthens an organization’s cybersecurity defenses, reducing the risk of cyberattacks and data breaches. Regulatory Compliance: Adherence to CMMC 2.0 demonstrates an organization’s commitment to meeting federal cybersecurity requirements and industry best practices.
CMMC’s purpose is to enhance the cybersecurity posture of organizations participating in the defense supply chain and achieves this via verifiable cybersecurity practices and processes. Companies must meet a specific level of cyber maturity before being awarded DoD contracts which ensures a greater likelihood that sensitive data and information stay secure throughout the supply chain.
Businesses aiming to work with or maintain existing contracts with the DoD must demonstrate their commitment to cybersecurity by complying with CMMC.
While the journey to CMMC compliance varies from one organization to another, experts recommend a number of best practices, categorized by phase, including baselining, implementation, enactment, and assessment. Baselining involves developing a plan with a consultant, determining if you manage CUI, creating a gap assessment, and creating POAMs. Implementation involves implementing the action items identified in the POAMs and the necessary procedures, training, and tools. Enactment involves implementing necessary monitoring of systems, training employees on new security requirements, and resolving outstanding issues. Assessment involves undergoing an audit by a C3PAO, preparing to present audit proof/evidence, and preparing for continuous improvement.
CMMC 2.0 Compliance Made Easy
Navigating the complex CMMC 2.0 ecosystem alone can be challenging. With the right guidance, tools, and resources, you’ll have peace of mind your organization’s cybersecurity posture aligns with – and even exceeds – the required standards.
By reading this guide, you’ve already taken the first steps toward achieving CMMC compliance and protecting your organization’s valuable data. Zog, Inc.’s team of cybersecurity experts are here to support you throughout the rest of the journey.
Get started today with a free 30-minute consultation and learn how we can help you streamline your journey toward CMMC 2.0 compliance.


Leave a Comment
Your email address will not be published. Required fields are marked *